
Mass migration to the online space has led to the widespread use of portable devices, especially mobile ones. It becomes more difficult to imagine users’ lives without mobile applications and constant information updates.
Ensuring data protection is one of the critical aspects of application development. And we are talking about both user data and the data of the application itself. It seems to be a banality. But too much depends on this banality to be neglected.
Mobile app security is important because modern applications are often available on multiple networks and connected to the cloud, making them more vulnerable to threats and security breaches. There is a growing need to provide mobile app security at the network level and the application level, and this approach is gaining more and more benefits. One reason is that hacker attacks are increasingly targeting applications. Mobile app security validation identifies weaknesses in the application layer, which can help prevent such attacks.
App Annie experts say that users spend 10 out of every 11 minutes on mobile apps. Given the role these IT solutions have come to play, many companies are concerned about the quality of applications, especially their security.
BetaNews research shows that 44% of applications contain personal data requiring a high-security level, and 66% use functionality to compromise user information privacy.
To ensure the security of the mobile apps they provide, companies rely on expert advice to provide security testing guidelines. This article is about common defects in this area and proper ways to prevent them.
Among mobile apps’ leaders in terms of installs, 94% contain at least three medium-risk vulnerabilities, and 77% have at least two critical ones.
An analyst shows difficulties with storing information and transferring data appear already in software development. And about 1/3 of applications contain hidden functionality and bottlenecks in the source code.
The figure below shows that these defects rank in the first three places as the most critical vulnerabilities in mobile applications. Let’s discuss them in more detail.
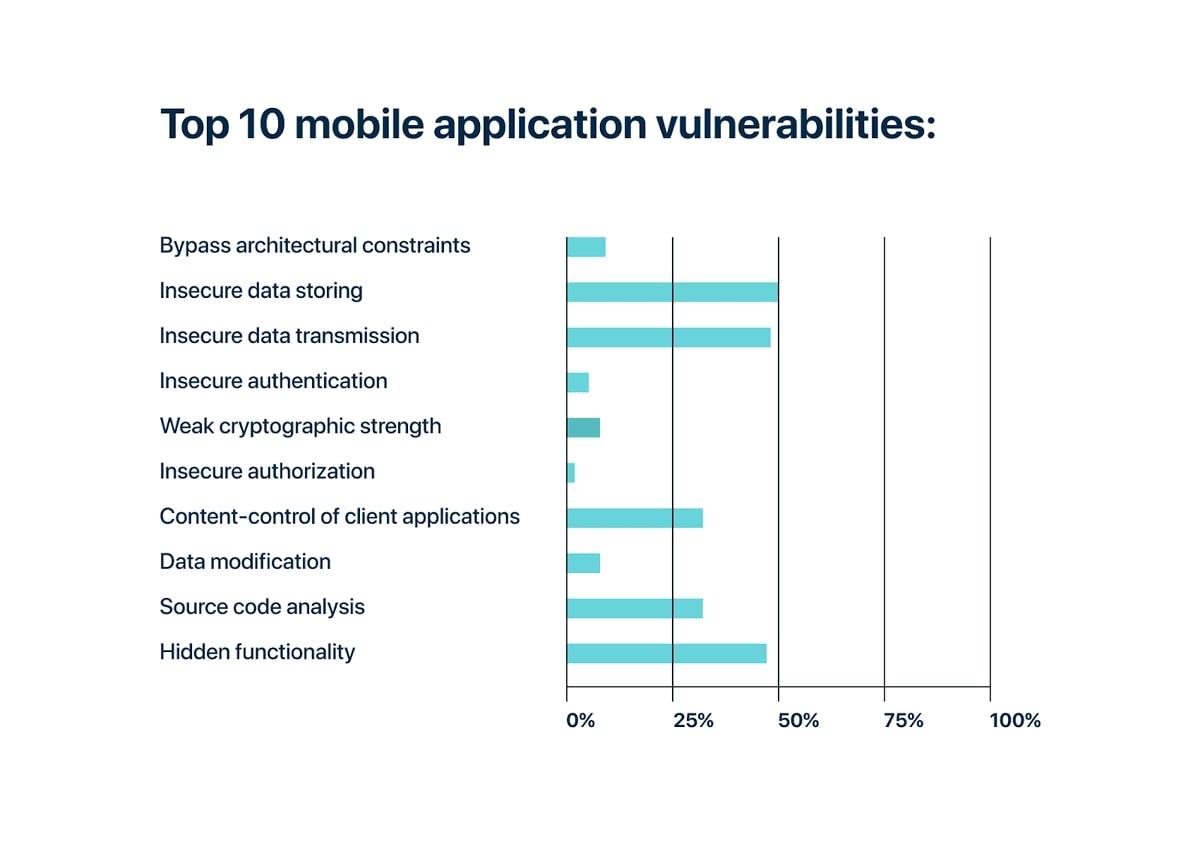
Compared to other types of devices, mobile phones are more at risk of being stolen or lost than others. But even if the physical copy of the device is with the user, companies should take more care of the proper storage of sensitive data (confidential information, etc.) to prevent intentional and unintentional leaks.
The issue is especially critical for software in banking and finance and healthcare: the insecurity of storing bank card numbers or nuances about patients’ health status in most cases can cause distrust on the part of users, which can lead to reputational losses, lawsuits, and scandals.
Interoperability between different platforms has become the norm for many applications. They are using a Google account when registering or paying online are some of those conveniences that users don’t want to give up. Using open APIs doesn’t only benefit customers. The integration of services provides end-users with a multifunctional and convenient application. This helps companies meet their business needs.
It is especially crucial to remember the risk of personal information leakage, which only becomes higher due to unsafe data transmission. It is important to remember to use TLS and SSL encryption methods and ensure that third-party services connected to the app comply with security requirements, including the minimum set of permissions, validating input from external sources, and much more.
About half of all analyzed applications contain hidden functionality to simplify debugging and testing of the application. But often, it remains even after the release, which makes it easier for fraudsters to hack data.
How can it happen? Attackers can download the application, examine the configuration files, view the code itself, and gain access to the software’s administrative part. All this can lead to confidential data disclosure, cryptographic extensions, theft of intellectual property, and much more.
Therefore, organizations should consider all possible scenarios and prevent potential risks by ensuring that the application runs securely.
Many companies are now using an agile methodology. Thanks to this, all security items are checked at each stage. So if your software provider uses this methodology, you can be sure of mobile app security.
One in four reviewers interviewed by the experts who compiled the World Quality Report 2019-2020 helped to optimize testing processes thanks to Agile. The statistics are as follows: if a company has introduced agile methodologies, then processes are accelerated by 75%, and cycles automatically become shorter due to more frequent releases.
That is why it is no longer enough to take care of mobile applications’ security at the last stages of the life cycle: critical defects often are found at the stage of production. It is much more expensive to fix them at later stages of the project. What’s more, having a robust early testing strategy, proactively identifying sensitive data, and building a threat mitigation model can help you avoid future security issues.
Almost every mobile application interacts with a back-end service where user data is stored. To prevent their leakage, security specialists simulate intruders’ actions, thereby checking the system for vulnerabilities.
The essence of penetration testing is to detect bottlenecks that cybercriminals can use for their purposes: stealing data, deliberately stopping the server, or restarting it. Prepare for such a reaction of the system and develop a plan for its recovery.
Process optimization is directly related to automation. Security testing is no exception. More than half of the respondents to the World Quality Report report that information security risks have decreased since testing automation.
Keep in mind, however, that full automation is not always ineffective. For example, automated vulnerability scans can skip critical combinations for the application. Therefore, develop appropriate QA strategies, considering the architecture, business logic, and system features.
While there was a lot of business time for security testing in 2019, only 13% of security checks are automated. And this is precisely the growth point for companies to think about in 2020 and further.
To keep your application secure, you should consider the most common vulnerabilities and prevent them from the very beginning.
With the help of recommendations, you can prevent them and get reliable software that meets all the necessary mobile app security standards.