
This post delves into seven effective options to bolster online payment security. By implementing these strategies, businesses can strengthen their ability to accept online payments from customers through credit cards while safeguarding sensitive data. These security measures positively impact your bottom line and reputation.
Reading time: 17 min.
Payment security in e-Commerce is a more relevant issue in 2023 than ever.
Since online purchases are often associated with ecommerce fraud, it’s imperative to prioritize addressing data storage challenges. Payment fraud poses a continuous security risk, always lurking around the corner. Therefore, online merchants must maintain constant vigilance, considering all potential avenues of identity theft to protect customers and ensure the security of each ecommerce website. Failing to do so may result in implementing superficial security measures, leaving vulnerabilities that competitors are more than willing to exploit for their advantage.
As per a study by DataProt, an astonishing “88% of adept hackers can infiltrate an organization’s defenses within a brief 12-hour window”.
If you want to maintain control of online payment security, use different elements of eCommerce payment security, for example, secure payment gateway and implementing two factor authentication.
In this post, IntexSoft will elaborate on these aspects of payment systems and more. You will discover the best security practices and find answers to the central question: “How can additional measures elevate your ecommerce payment security to a new level?”
Ecommerce security refers to the various measures and technologies businesses use to keep sensitive payment information safe when you monitor transactions. These steps are like a protective shield, ensuring that your payment details are kept secure and that no one can access payment systems without robust customer authentication.
In ecommerce, payment security ensures businesses are protected from fraud while verifying a user’s identity online.
But occasionally, security breaches can throw curve balls at your online store. According to figures published by Cyber Angel’s report, more than 70 billion exposed files were detected (including financial & sensitive information). And that’s when you might need assistance. This point is where security practices can make a significant difference, addressing the financial and legal penalties that often arise. You can be proactive and foresee such challenges. To prevent security breaches, you, as an online store owner, can adopt the best security practices, which we will learn in the next section.
Let’s get into it right now!
Strong passwords and two factor authentication (2FA) are fundamental security measures.
Elaborate passwords serve as the initial layer of protection against unauthorized entry to your online shop. Here’s why they matter:
Benefits of robust passwords
| Avoiding brute force attacks |
Hackers often attempt to crack passwords in payment systems using automated tools that try different combinations. Make these attacks significantly more challenging not least of all – due to complex passwords. Mix uppercase, lowercase, numbers, and symbols. Use longer passwords (at least 12 characters).
|
| Safeguarding customer data |
Your online store likely collects sensitive customer data, such as payment details and personal info. A breach could lead to financial and reputational damage. Strong passwords aid in averting unauthorized entry to this valuable information.
|
| Defending against unauthorized changes |
A compromised admin account could allow malicious individuals to make unauthorized changes to your website, affecting its functionality or appearance. With robust passwords only authorized personnel can make modifications.
|
While strong passwords are an important aspect of ecommerce security, they can’t guarantee 100 percent protection from attacks. That’s why the next wise decision is to utilize 2FA.
Two-factor authentication’s benefits
| An extra level of ecommerce security |
2FA demands customers to furnish two types of identification as a prerequisite for accessing an account. This commonly entails knowledge-based information (password), and information depends on a specific mobile device or authentication app.
|
| Defense against pilfered login information |
In this context, a unique code is the crucial element for accessing an account, which can only be generated on a mobile app. Hence, even if a hacker acquires the correct password, they still require this additional code, acting as a safeguard. This approach helps you avoid appearing careless or irresponsible and showcases your foresight as a business owner. The truth is additional security measures against stolen credentials are never superfluous.
|
| Enhanced trust |
Implementing 2FA demonstrates a commitment to ecommerce security. Users are more likely to feel safe and share payment data and make transactions on your platform.
|
Implementing 2FA:
SSL certificates prevent fraudulent transactions by creating a secure link between a web server and a customer’s browser through encryption. This is a practical guarantee that all the data remains confidential. That’s why SSL certificates make shopping online secure.
The importance of SSL certificates can be highlighted with three dominant benefits. Refer to the table below.
Benefits of SSL certificates
| Data encryption |
These certificates encrypt important data, making it indecipherable to anyone attempting to intercept it.
|
| Trust and credibility |
Websites with SSL certificates display a lock symbol in the browser’s address bar, signifying a secure connection. This visual cue instills trust in users, assuring them that information, including cardholder data (billing address), is safe.
|
| SEO |
Secure websites are always given preference in search engine rankings. An SSL certificate can boost your site’s search position, potentially increasing traffic.
|
Implementing SSL certificates:
PCI standards refer to rules and demands jointly established by major credit card companies (Visa, MasterCard, or American Express). These standards aim to thwart any potential data breaches.
Here are some key points regarding the implementation and maintenance of PCI standards:
Selecting an appropriate payment processor is the most secure approach to ensure compliance with PCI DSS. It’s essential to collaborate with a payment processor who comprehends credit card payments and demonstrates expertise in this domain. This partnership is important to safeguarding sensitive financial information and maintaining the highest security standards in payment processing.
The magic of tokenization is this: it replaces sensitive data (IDs with a unique code or credit card numbers) with a token. This token looks like a decoy, doesn’t have real value, and throws cyber crooks for a loop when they’re trying to nab valuable payment information.
Now, let’s break down some of the key points of token-based security:
Benefits of tokenization
| Protection from data breaches |
Tokenization ensures ecommerce payment data and other confidential information never sits out there in the wild. Instead, it’s substituted with a token that’s generated randomly.
|
| Enhanced security |
Unlike old-school encryption, which can be unlocked with the correct key, tokens have no direct connection to the original data. It’s like putting a lock on a lock – extra security layers to fend off every data breach.
|
| Compliance |
Tokenization stands shoulder to shoulder with important regulations. A typical example is the Payment Card Industry Data Security Standard. These regulatory measures are a prime point for enterprises that depend on ecommerce payment.
|
| Reduced risk and data protection |
Less sensitive data means less risk. Those stolen tokens are empty shells, even if a data breach happens.
|
| Simplified compliance audits |
With less sensitive data to worry about, businesses can save time and have an easier time with compliance audits.
|
| Versatility |
You can employ tokenization across various domains – for online payments, healthcare records, and customer profiles. This versatility is why we refer to it as a multifaceted, magical toolkit for diverse industries.
|
This technique converts regular text into ciphertext, rendering it indecipherable to would-be cyber intruders unless they possess the decryption key. However, obtaining this key is a complex challenge for them. This process always relies on the following:
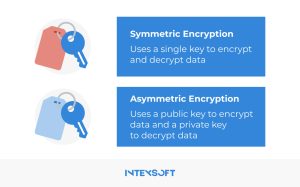
Encrypting data benefits
| Preserving the secrecy of information |
Encryption guarantees that, even if online payment data ends up in unauthorized users, it will be utterly ununderstandable.
|
| Protection against data breaches |
In a security breach or strange access, your payment system can maintain encrypted information safe from exploitation.
|
| Compliance |
Many industries and regulatory bodies mandate encryption to protect sensitive information, ensuring legal compliance.
|
| Secure communication |
Encryption is crucial for ensuring data safety while it is in transit, such as online purchases, email communications, and more.
|
An address verification system, sophisticated algorithms, and machine learning to monitor real-time transactions are valuable elements of detecting possible attacks. You can spot irregularities or patterns consistent with fraudulent activities using these components and sort them out. Immediately.
These systems analyze user behavior and transaction patterns, flagging deviations from typical activity. For instance, sudden purchasing behavior changes or multiple failed login attempts can trigger alerts. By identifying common fraud patterns, such as unusual payment locations or a series of transactions with similar characteristics, detection systems can issue warnings and halt potentially fraudulent transactions.
Benefits for businesses:
One crucial step is to provide cybersecurity training for your staff. This process covers various topics, including proper email etiquette and physical security measures. Here are some key points to consider:
To conduct practical staff training, consider these strategies:
In this post, we have delved into several trusted security measures that business owners are probably familiar with – SSL certificates, tokenization, maintaining PCI compliance, data encryption, and other elements of secure payment gateway, keeping an eye on ecommerce fraud.
Do you need assistance in e-commerce payment security and choosing reliable payment processors? Our team of experts is here to address any challenges you may encounter. Our top priority is ensuring the highest level of protection for your ecommerce transactions. Contact IntexSoft now.
Payment security in e-commerce is the protection of sensitive data during online transactions. It involves encryption, SSL certificates, PCI DSS compliance, tokenization, MFA, fraud detection, and regular audits of ecommerce security threats. The goal is to prevent data breaches, loss of user accounts and building customer trust.
Here is a concise list of security measures used in ecommerce business:
There are main e-commerce security principles that online stores should consider:
To safeguard your e-commerce customers’ data and privacy, you should securely store sensitive information, such as customer payment data, by building a solid verification system. This process involves implementing encryption, secure authentication, authorization, and establishing dependable backup and recovery processes. These measures are essential in preventing unauthorized access, tampering, or accidental data theft. As a result, your customers’ information will remain very well-protected.